Avoiding Limitations of Traditional Approaches to Security
Best practice advice for cloud and container security
In securing cloud and hybrid environments, some organizations try to replicate the traditional security stack they use for their on-premises infrastructure. Although they typically face the same security requirements when locking down cloud assets, the tools they have available to them and how they implement those tools are different. To get a better understanding of the practical differences between the traditional security stack and building a layered security strategy for a cloud infrastructure, we asked our experts the following question: What limitations can you expect when stitching together multiple security solutions in a cloud infrastructure?
By submitting this form, you agree to our privacy policy
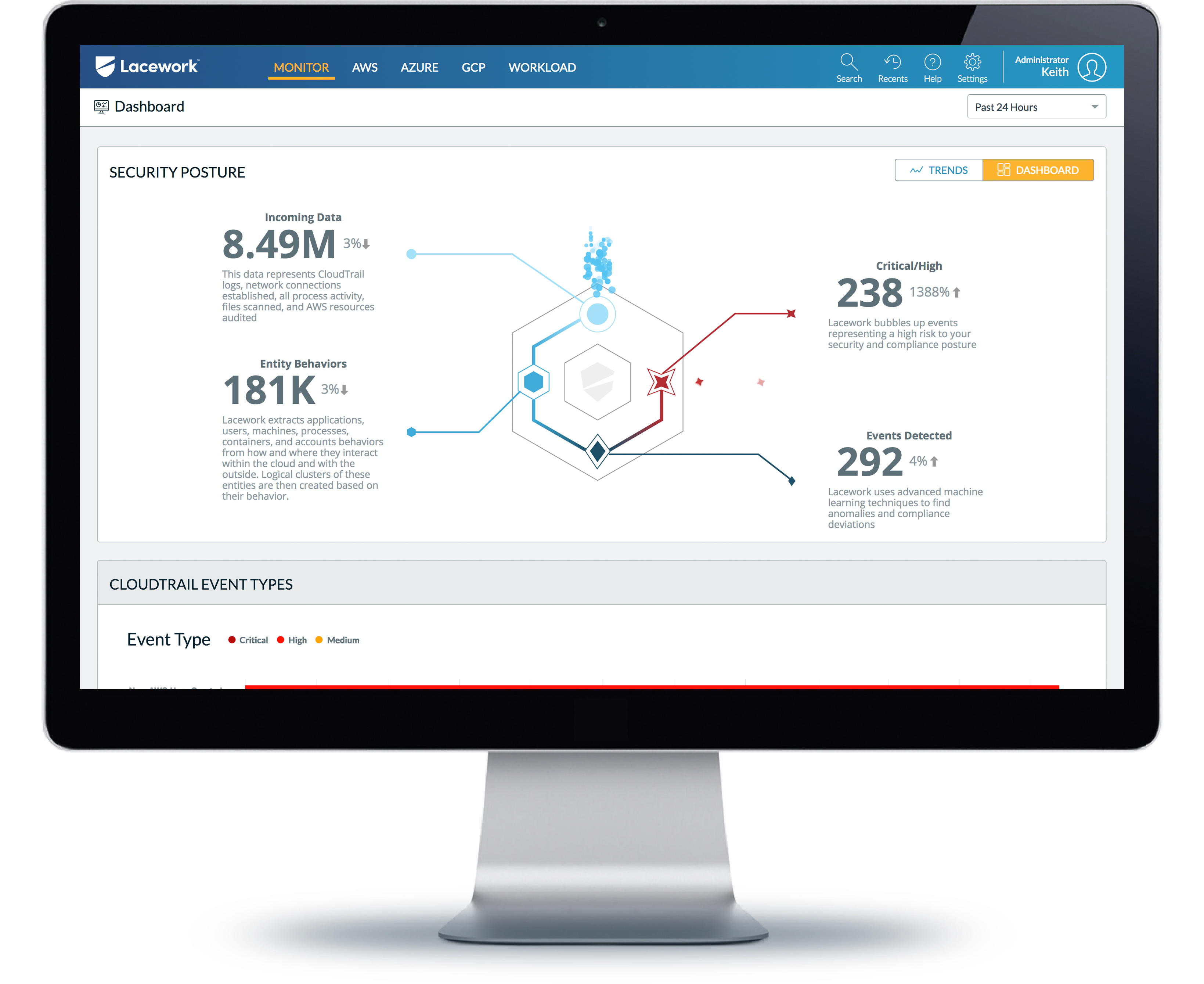
Know your environment
Get a detailed custom report identifying compliance misconfigurations, vulnerabilities, anomalies, or hidden threats within your cloud footprint.