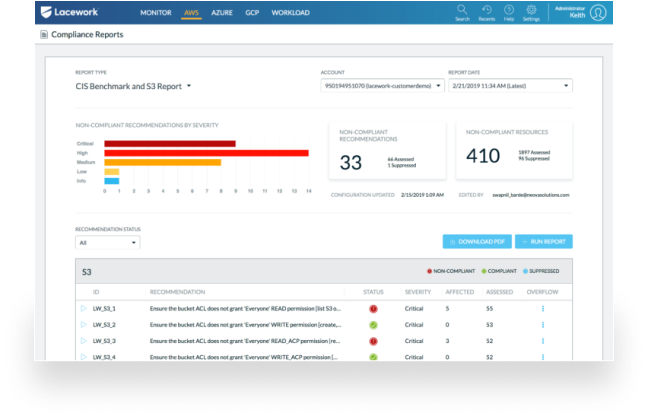
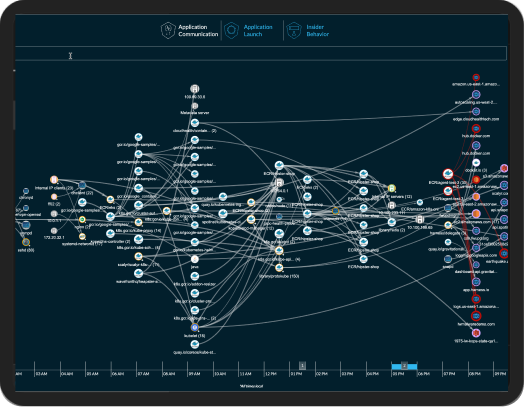
Thank you for [x, y, z...]!
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor
- Recent botnet activity including Sysrv-Hello and GroundHog DDoS Botnet that rapidly infects the cloud
- The rise of Supply Chain threats and attacks
- Highlights of Lacework’s Tactics, Techniques, and Procedures (TTPs) around building and tracking